File Security Articles
-
·
5 Common Email Mistakes That Put Sensitive Data at Risk — And How to Avoid Them
In today’s digital-first business environment, email remains one of the most widely used tools for communication and file sharing. But for organizations handling sensitive data, such as legal contracts, financial statements, health records, and proprietary business information, email can also be a significant security risk. Cybercriminals constantly seek new ways to exploit email vulnerabilities. Whether
-

·
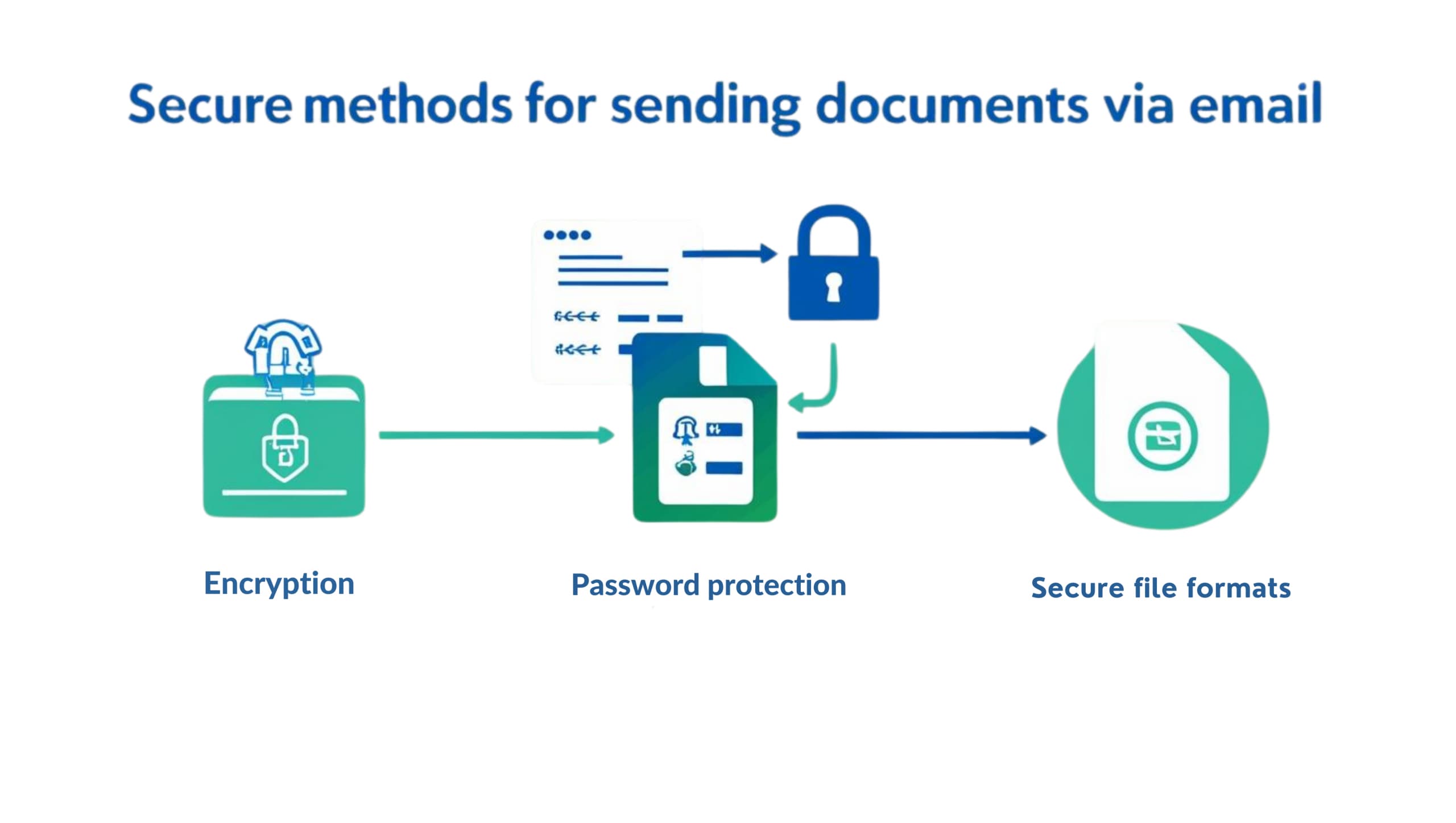
How to Send Documents Securely via Email
Email remains one of the most widely used tools for business communication, but when it comes to sending confidential documents, it’s also one of the most vulnerable. From data breaches to accidental leaks, one simple misstep in document transmission can lead to regulatory issues, reputational damage, or financial loss. Whether you’re sharing sensitive business contracts,
-

·
The Sushi Wars and Data Security
On February 26, 2024, the Tokyo District Court convicted Kappa Sushi of violating the Unfair Competition Prevention Act (trade secret infringement) for Kappa Sushi’s fraudulent use of Hama Sushi’s trade secrets. This incident occurred in 2020 when a former executive, who changed his job from Hama Sushi to Kappa Sushi, obtained a file containing trade
-

·
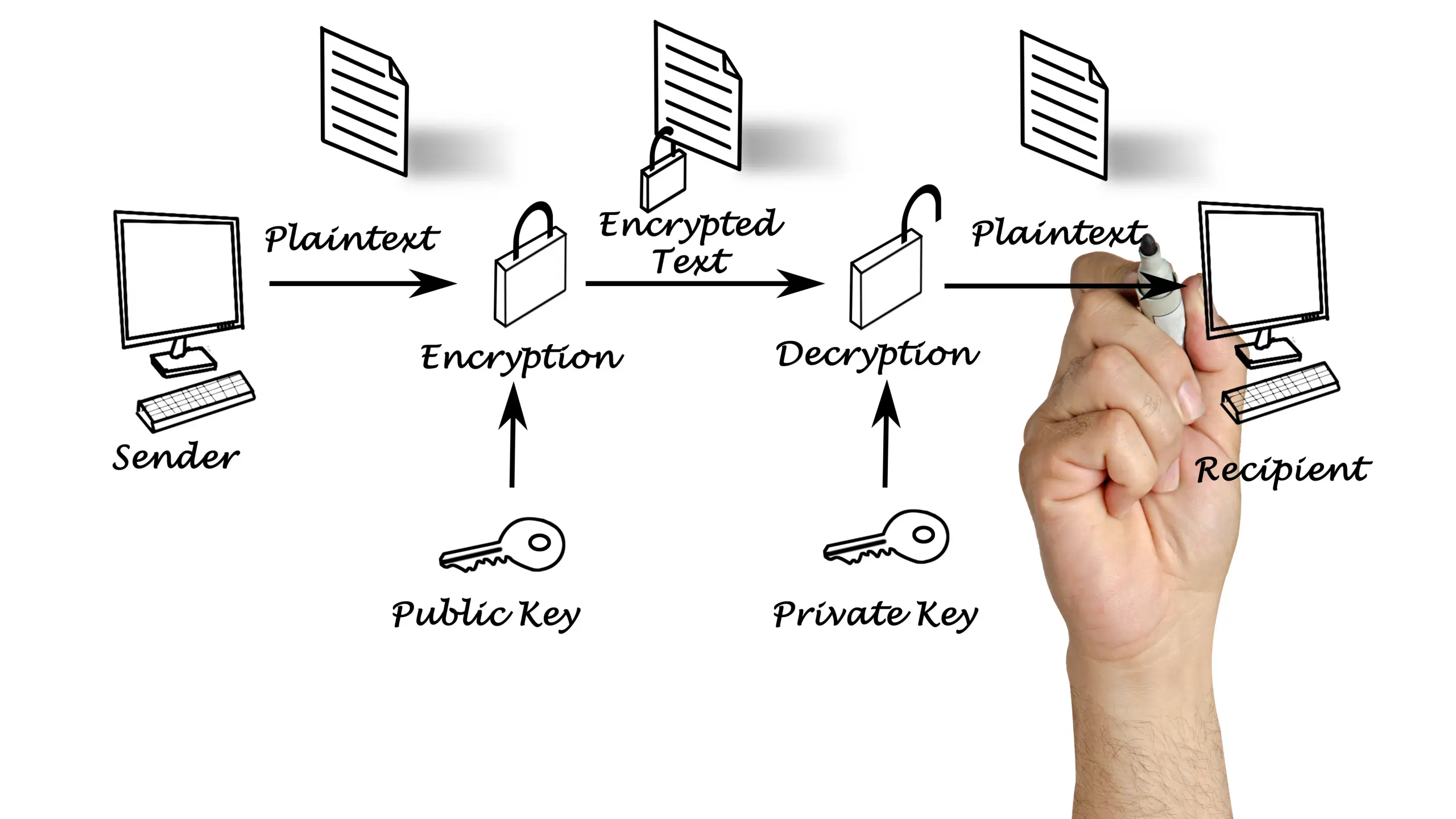
What is IRM, and Why You Should Use It?
What is IRM, and Why You Should Use It Information Rights Management (IRM) is a combination of technologies that control and manage access to sensitive information or digital content. The reasons for using IRM are to safeguard sensitive data, prevent unauthorized access, and control how authorized users can use that information. Compared to password protection
-

·
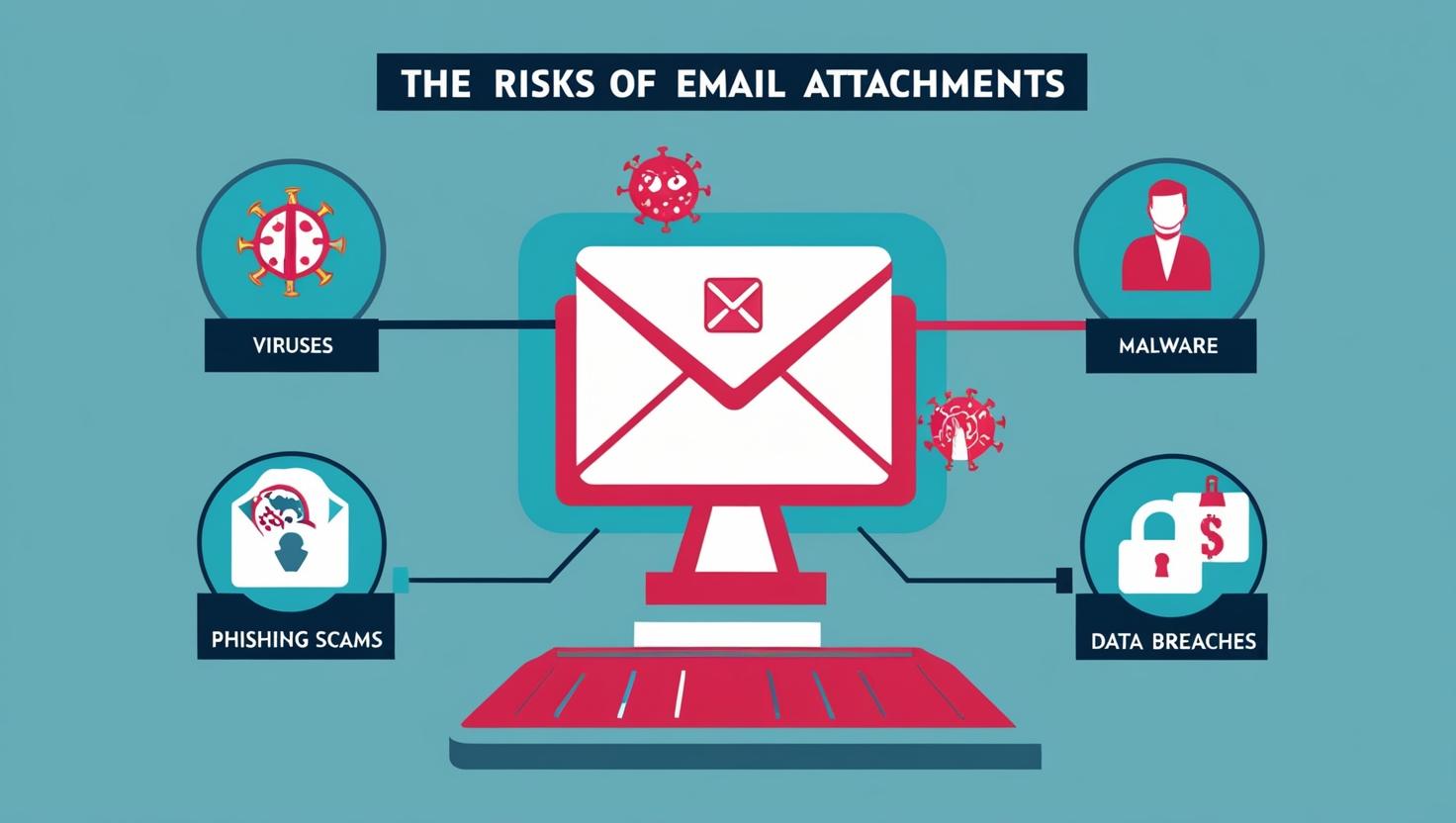
The Risks Of E-Mail Attachments
Why Sending Email Attachments Is Putting Your Business at Risk (And What to Do Instead) Email remains one of the most widely used tools for business communication — and one of the most common ways sensitive files are shared. But while email attachments are convenient, they also pose a serious risk to your organization’s data
-

·
How Content Security Could Have Prevented The Fukuoka COVID-19 Patient Data Breach
On January 6, 2021the Fukuoka prefectural government of Japan announced that the names, location, and age of 9500 people infected with COVID-19 had been leaked on the Internet. The breach occurred when a government employee mistakenly sent a link to the Excel file stored on Google Drive to an outsider. The file was accessible via
-

·
How Dangerous Is Cheating On Exams In Many Different Ways
It is convenient to conduct online exams. As a private learning center or educational institution, you don’t need to worry about location constraints as students can do the exam anywhere. Provided that they have access to a computer with an internet connection, it is also relatively easy and cheap to conduct online exams. However, with
-

·
How To Share Internal Documents Securely?
You want to securely and efficiently share email attachments? You don’t want your documents to be exposed? You can’t also control who viewed or downloaded your documents? No matter what industry you are in, it is extremely important to secure attachments when sending out via email to avoid unnecessary risks and losses. For the education
-

·
Show It, Don’t Send It
You’re Sharing Files All Wrong — Here’s How to Do It Right (and Securely) File sharing is critical to daily operations, whether it is sending pricing proposals, investor decks, or product roadmaps, most organizations rely on tools like email, Google Drive, or Dropbox to share documents quickly. But here’s the problem: the very tools that