Blogs
-

·
How To Secure Files For ISO 27001 Compliance ISO 27001 File Sharing Guide
Introduction Sharing files — whether internally between teams or externally with partners and clients — is essential for day-to-day business. But without proper safeguards, a single misplaced document can lead to serious consequences: data breaches, regulatory fines, and long-term damage to your company’s reputation. For organizations serious about information security, ISO/IEC 27001 is the global…
-

·
Our Predictions For The Internet In 2025
What CIOs and CISOs Need to Know About Internet Trends, Surveillance, and Secure File Sharing As the digital landscape rapidly evolves, the challenges for CIOs and CISOs have become more complex. The past year highlighted growing threats from surveillance, AI misuse, censorship, and weakened data privacy enforcement. In this article, we’ll examine key cybersecurity trends…
-

·
5 Common Email Mistakes That Put Sensitive Data at Risk — And How to Avoid Them
In today’s digital-first business environment, email remains one of the most widely used tools for communication and file sharing. But for organizations handling sensitive data, such as legal contracts, financial statements, health records, and proprietary business information, email can also be a significant security risk. Cybercriminals constantly seek new ways to exploit email vulnerabilities. Whether…
-

·
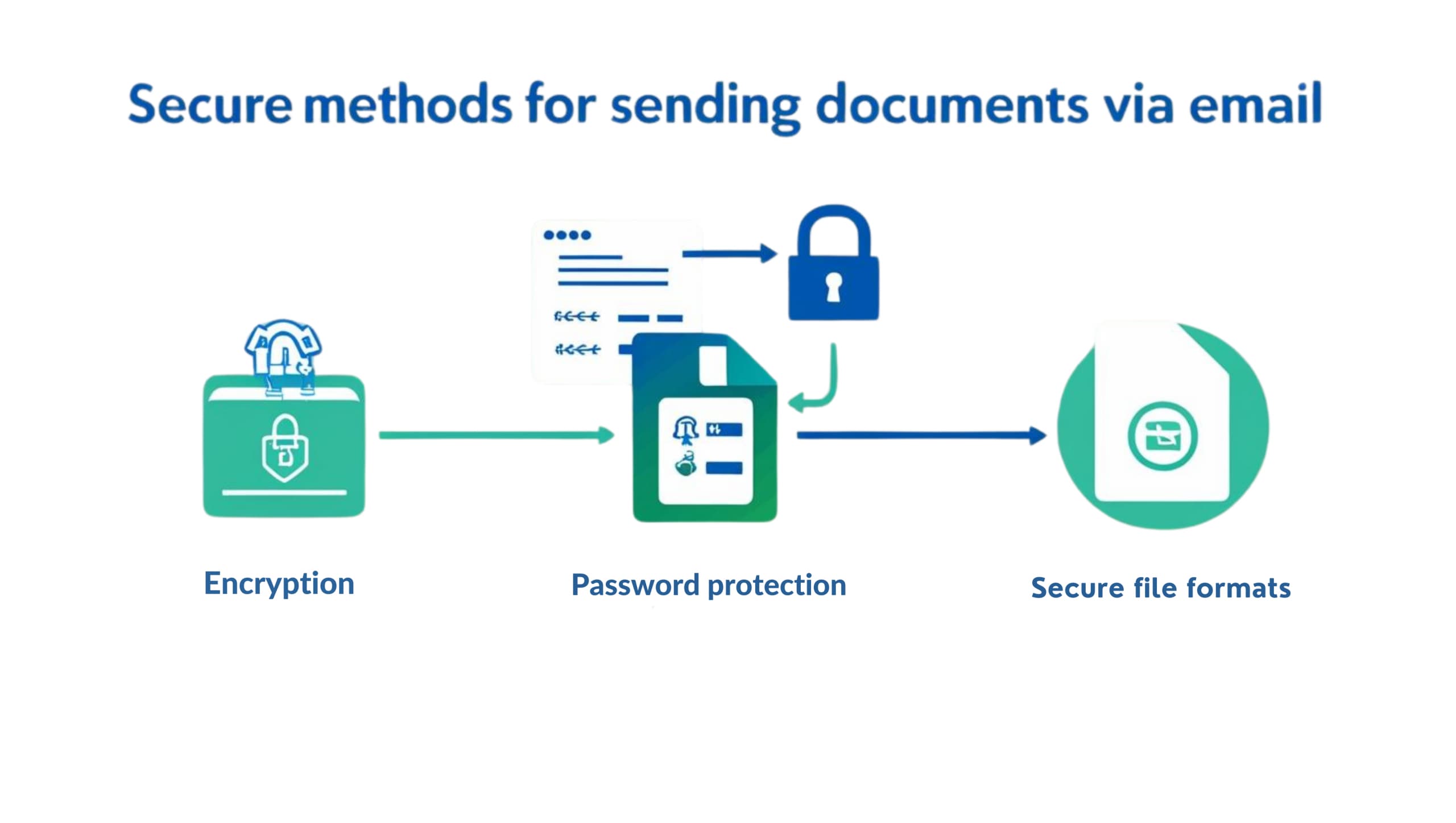
How to Send Documents Securely via Email
Email remains one of the most widely used tools for business communication, but when it comes to sending confidential documents, it’s also one of the most vulnerable. From data breaches to accidental leaks, one simple misstep in document transmission can lead to regulatory issues, reputational damage, or financial loss. Whether you’re sharing sensitive business contracts,…
-

·
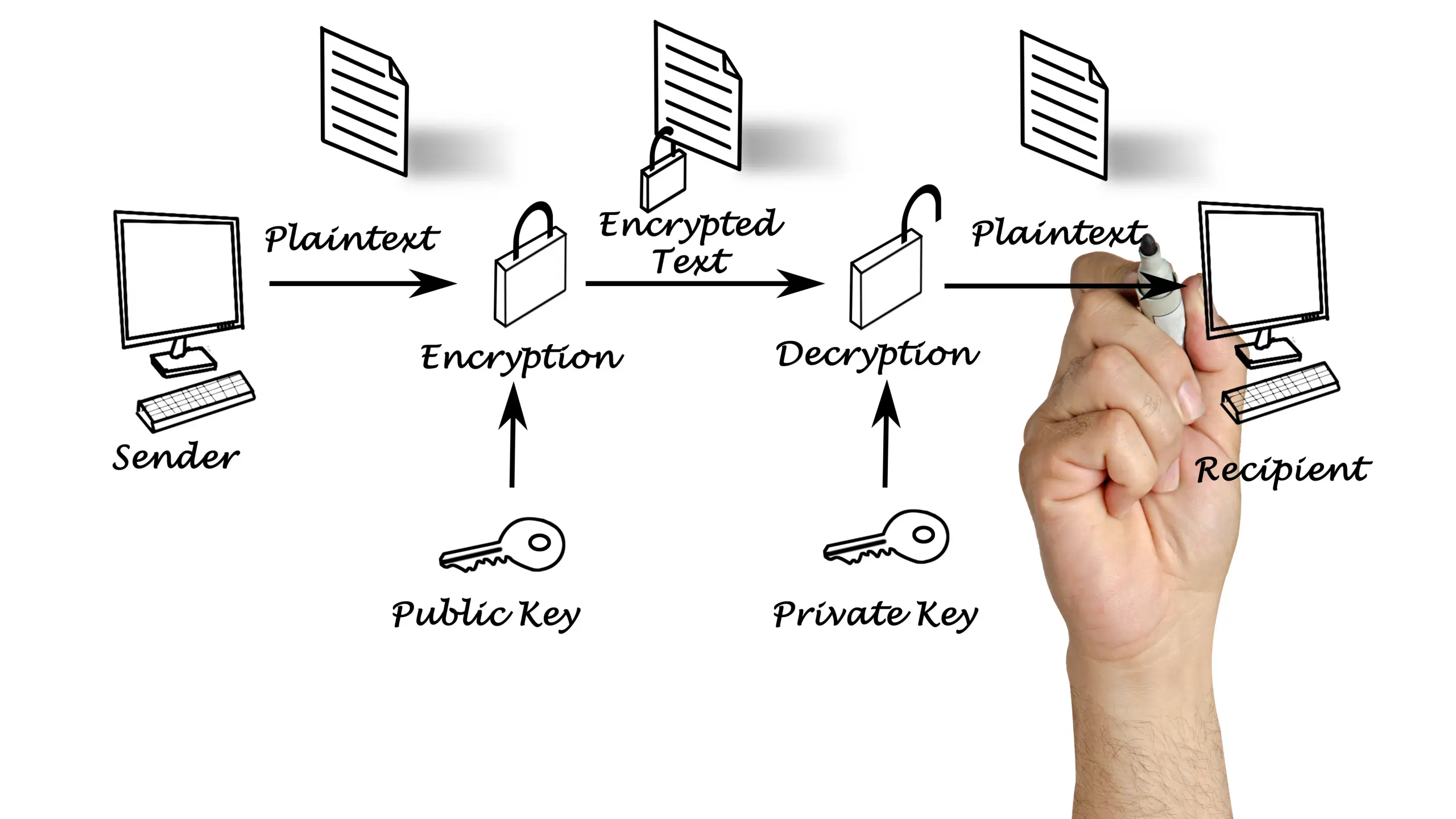
What is IRM, and Why You Should Use It?
What is IRM, and Why You Should Use It Information Rights Management (IRM) is a combination of technologies that control and manage access to sensitive information or digital content. The reasons for using IRM are to safeguard sensitive data, prevent unauthorized access, and control how authorized users can use that information. Compared to password protection…
-

·
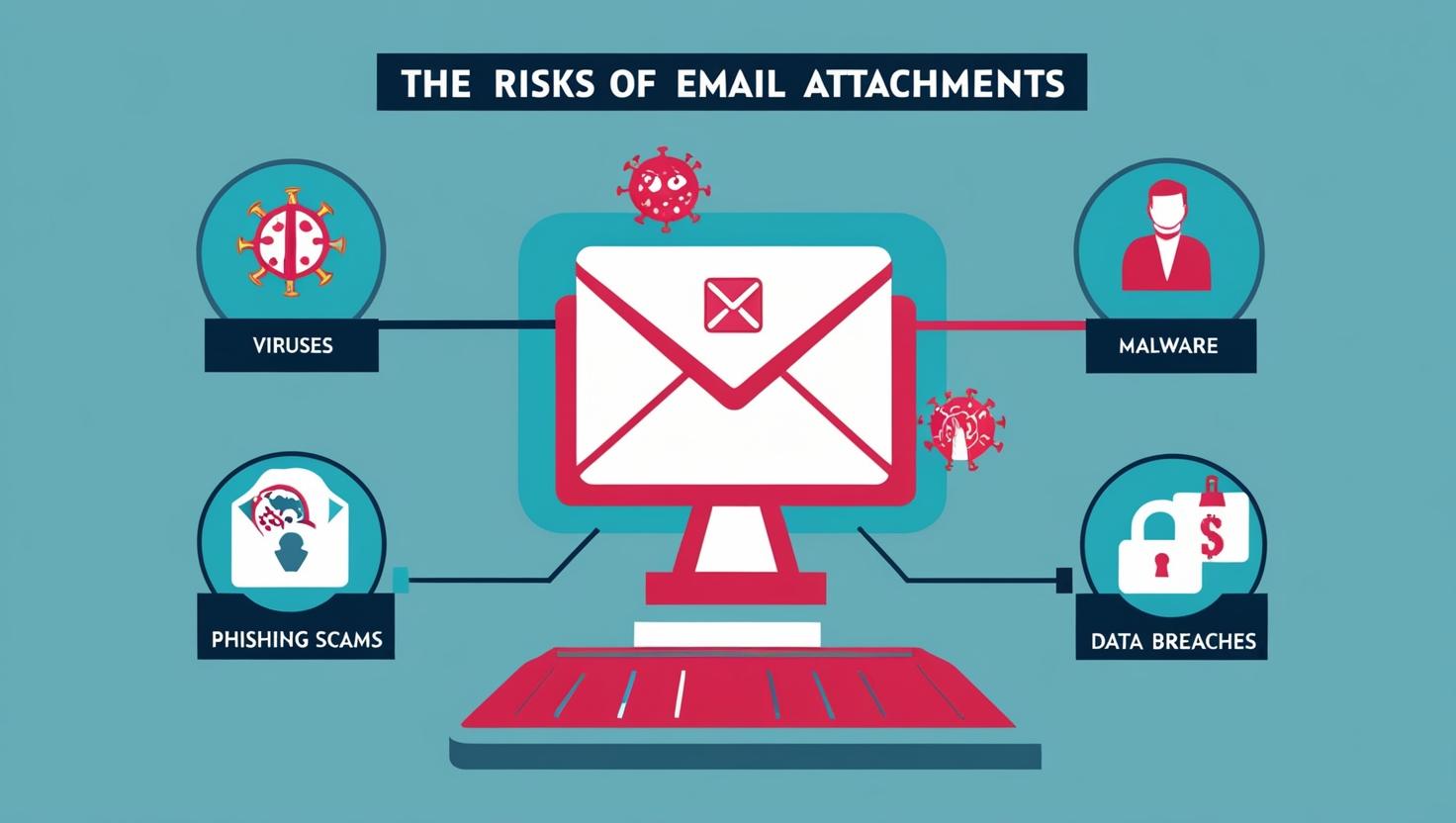
The Risks Of E-Mail Attachments
Why Sending Email Attachments Is Putting Your Business at Risk (And What to Do Instead) Email remains one of the most widely used tools for business communication — and one of the most common ways sensitive files are shared. But while email attachments are convenient, they also pose a serious risk to your organization’s data…
-

·
Why Secure Email Attachments Matter: Protecting Confidential Documents Across Industries
Email remains one of the most common ways to share files in business today. But traditional email attachments pose serious security risks, especially when those files contain confidential, proprietary, or personally identifiable information. Whether you work in education, design, finance, or enterprise IT, your documents are valuable and vulnerable. Once an email is sent, the…
-

·
Show It, Don’t Send It
You’re Sharing Files All Wrong — Here’s How to Do It Right (and Securely) File sharing is critical to daily operations, whether it is sending pricing proposals, investor decks, or product roadmaps, most organizations rely on tools like email, Google Drive, or Dropbox to share documents quickly. But here’s the problem: the very tools that…
-

·
Red Bull Vs. Aston Martin In Possible IP Breach
Formula One is the pinnacle of motorsports and automotive technology. It is a multi-billion-dollar industry that is underpinned by the intellectual property that enables the teams to produce the fastest cars in the world. Last week, at the Spanish Grand Prix, the Aston Martin team introduced an upgraded car that in many aspects looked very…